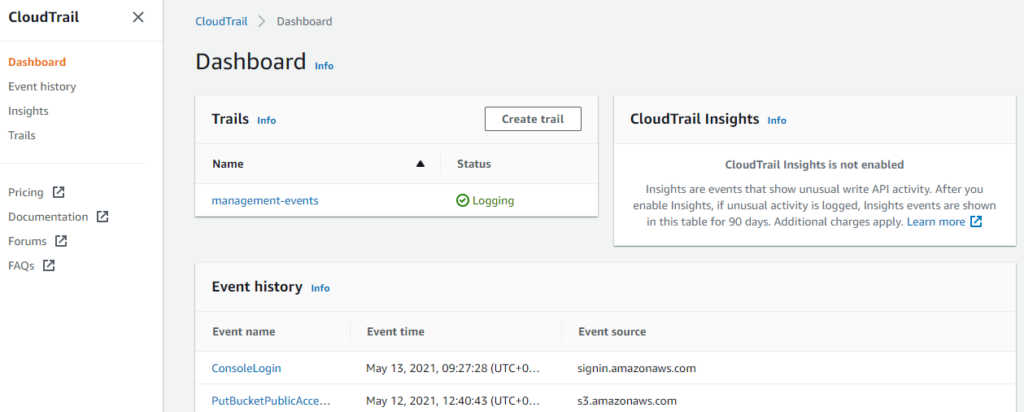
AWS CloudTrail
AWS CloudTrail
AWS CloudTrail is a service that enables governance,
compliance, operational auditing, and risk auditing of your AWS
account.
With CloudTrail, you can log, continuously monitor, and retain
account activity related to actions across your AWS
infrastructure.
CloudTrail provides event history of your AWS account activity,
including actions taken through the AWS Management Console, AWS
SDKs, command line tools, and other AWS services
Solutions can be implemented with this service:
1. With AWS CloudTrail, simplify your compliance audits by
automatically recording and storing event logs for actions made
within your AWS account. Integration with Amazon CloudWatch Logs
provides a convenient way to search through log data.
2. AWS CloudTrail increases visibility into your user and resource
activity by recording AWS Management Console actions and API
calls. You can identify which users and accounts called AWS,
the source IP address from which the calls were made, and when
the calls occurred.
3. With AWS CloudTrail, you can discover and troubleshoot security
and operational issues by capturing a comprehensive history of
changes that occurred in your AWS account within a specified
period of time.
AWS CLoudTrail has the following use cases:
1. AWS CloudTrail makes it easier to ensure compliance with
internal policies and regulatory standards by providing a
history of activity in your AWS account.
2. You can perform security analysis and detect user behavior
patterns by ingesting AWS CloudTrail events into your log
management and analytics solutions.
3. You can detect data exfiltration by collecting activity data
on S3 objects through object-level API events recorded in
CloudTrail. After the activity data is collected, you can use
other AWS services, such as Amazon CloudWatch Events and AWS
Lambda, to trigger response procedures.
4. You can troubleshoot operational issues by leveraging the AWS
API call history produced by AWS CloudTrail. For example, you
can quickly identify the most recent changes made to resources
in your environment, including creation, modification, and
deletion of AWS resources.
5. You can detect unusual activity in your AWS accounts by enabling
CloudTrail Insights. For example, you can quickly alert and act
on operational issues such as erroneous spikes in resource
provisioning or services hitting rate limits.
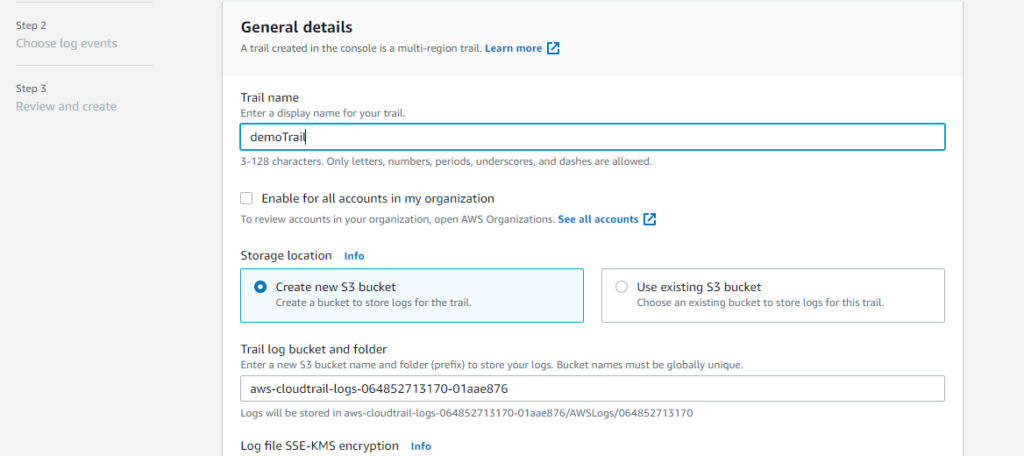
AWS CLoudTrail Features:
1. AWS CloudTrail is enabled on all AWS accounts by default and
records your account activity upon account creation. You can
view and download the last 90 days of your account activity for
create, modify, and delete operations of supported services
without the need to manually setup CloudTrail.
2. You can view, search, and download your recent AWS account
activity. This allows you to gain visibility into changes in
your AWS account resources so you can strengthen your security
processes and simplify operational issue resolution.
3. You can validate the integrity of AWS CloudTrail log files
stored in your Amazon S3 bucket and detect whether the log
files were unchanged, modified, or deleted since CloudTrail
delivered them to your Amazon S3 bucket.
4. By default, AWS CloudTrail encrypts all log files delivered to
your specified Amazon S3 bucket using Amazon S3 server-side
encryption (SSE). Optionally, add a layer of security to your
CloudTrail log files by encrypting the log files with your AWS
Key Management Service (AWS KMS) key. Amazon S3 automatically
decrypts your log files if you have decrypt permissions.
5. By enabling data event logging in CloudTrail, you can record
object-level API activity, and receive detailed information
such as who made the request, where and when the request was
made, and other details. Data events record the resource
operations (data plane actions) performed on or within the
resource itself. Data events are often high volume activities.
CloudTrail data event logging includes operations such as
Amazon S3 object level APIs, AWS Lambda function Invoke APIs,
and Amazon DynamoDB item-level APIs.
6. Management events provide insights into the management
(“control plane”) operations performed on resources in your
AWS account. For example, you can log administrative actions
such as creation, deletion, and modification of Amazon EC2
instances. For each event, you can get details such as the AWS
account, IAM user role, and IP address of the user that
initiated the action, time of the action, and which resources
were affected.
7. CloudTrail Insights can be used to detect unusual activity in
your account, such as bursts of IAM actions or inaccurate
resource provisioning or hitting service limits or gaps in
periodic maintenance and so on. You can enable CloudTrail
Insights events across your AWS organization, or in individual
AWS accounts in your CloudTrail trails.
8. CloudTrail can also be integrated with other services such as
AWS lambda, CloudWatch Logs and CloudWatch Events.
9. CloudWatch Logs allows you to create metric filters to monitor
events, search events, and stream events to other AWS services,
such as AWS Lambda and Amazon Elasticsearch Service.
10. AWS CloudTrail integration with Amazon CloudWatch Logs enables
you to send management and data events recorded by CloudTrail
to CloudWatch Logs. CloudWatch Logs allows you to create metric
filters to monitor events, search events, and stream events to
other AWS services, such as AWS Lambda and Amazon Elasticsearch
Service.
11. AWS CloudTrail integration with Amazon CloudWatch Events
enables you to automatically respond to changes to your AWS
resources. With CloudWatch Events, you are able to define
actions to execute when specific events are logged by AWS
CloudTrail. For example, if CloudTrail logs a change to an
Amazon EC2 security group, such as adding a new ingress rule,
you can create a CloudWatch Events rule that sends this
activity to an AWS Lambda function. Lambda can then execute a
workflow to create a ticket in your IT Helpdesk system.
Related
0
Votes
3
Ans
How to Switch Java Version on Linux Using Alternatives Command
1.64K viewsvarelite Changed status to publish
Question and answer is powered by anspress.net
Loading repositories and latest updates...
Recent Posts
Recent Blog
- heating_impn on Installation of Linux Operating System (Red Hat 8) in VMWare Workstation
- global_xvPn on Installation of Linux Operating System (Red Hat 8) in VMWare Workstation
- 2jl on In Azure: Canonical Ubuntu Issue Impacted VMs and AKS
- 2jl on In Azure: Canonical Ubuntu Issue Impacted VMs and AKS
- 2jl on What is Cloud Computing?
Interview Q&A
- September 2025
- August 2025
- July 2025
- June 2025
- May 2025
- March 2025
- November 2024
- October 2024
- September 2024
- July 2024
- June 2024
- May 2024
- March 2024
- February 2024
- January 2024
- November 2023
- October 2023
- September 2023
- August 2023
- July 2023
- April 2023
- March 2023
- January 2023
- December 2022
- November 2022
- October 2022
- September 2022
- August 2022
- May 2022
- April 2022
- March 2022
- February 2022
- January 2022
- November 2021
- September 2021
- August 2021
- July 2021
- June 2021
 Visit My GitHub VARELITE
Visit My GitHub VARELITE